Single Sign In with SAML
☝️ This feature is only available to workspaces using the Enterprise Plan.
What is SAML?
SAML (Security Assertion Markup Language) is a standard for SSO (single sign on). SAML allows your users to sign in to Kutano using your enterprise SSO Identity Provider.
In a nutshell, your organization can run its own SAML server to authenticate users. So you get to control password strength, two-factor authentication and restricting access to removed accounts for all your SAML-enabled SaaS apps in one place. See Wikipedia's SAML article for more background details.
How do I get a SAML Server?
There are many service providers who offer SAML solutions including Google Workspace, Microsoft Entra ID (formerly Microsoft Azure Active Directory or Azure AD), Okta, and more.
How to Configure SAML SSO
In order to configure SAML SSO you will need to configure both the identity provider and your Kutano workspace.
SAML uses the following naming convention for the two parts of the sign in service:
Identity Provider (IdP) - the enterprise SSO provider. For example, Google Workspace, or Microsoft Entra ID.
Service Provider (SP) - Kutano will be the service provider.
Configuring Kutano for SAML
First, you will need to sign in to Kutano as a workspace administrator. To access the SAML setting, navigate to Workspace admin -> Workspace settings using the sidebar. Scroll down to the until you see the Single sign on section.
Click on the edit icon to view the settings.
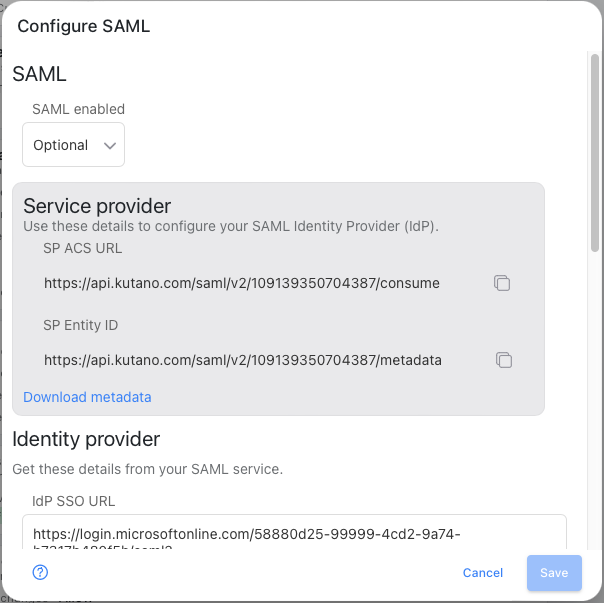
The first step is to enable SAML for the workspace.
In the SAML Enabled field select Optional or Required. Optional allows your user to use sign in with SAML or their user and password. You will now be able to specify the SAML settings.
The Service provider section displays information from the Kutano system that will be used to configure your SAML identity provider. Kutano provides the ACS URL and the SP Entity ID.
The ACS URL is the location an Identity Provider redirects its authentication response to. It needs to be set by the enterprise when configuring your Kutano in their identity provider's administration dashboard.
The SP Entity ID is a URI used to identify the issuer of a SAML request, response, or assertion. In this case, the entity ID is used to communicate that Kutano will be the party performing SAML requests to the enterprise’s identity provider.
You can click on the icons next to each field to copy the information and then paste it into the identity provider configuration screens.
Additional instructions and details are available for Google Workspace and Microsoft Entra ID providers.
When you have finished configuring your identity provider you can scroll down the page to where you are able to configure Kutano.

Fill out the IdP fields based on information found on your enterprise's identify provider.
You can also specify a custom Button name that your users will see when they navigate to the Kutano sign-in dialog.