SAML with Google Workspace
☝️ This feature is only available to workspaces using the Kutano Enterprise Plan.
If you haven't already done so, start by reading up on the general setup of SAML with Kutano.
Here's a walk-through of setting up Google Workspace (formerly known as G-Suite or Google Apps for Work) as your SAML Identity Provider. With this SAML connection in place, your team can sign into Kutano simply by being logged into their Google account.
NOTE: You may also want to refer to the Google documentation regarding SAML application setup.
Setup
To make this setup easier, it's a good idea to have both the Google Workspace Admin Console and the Kutano workspace administration screen opened in separate browser windows or tabs so you can copy data from one web page to the other.
Sign in to Kutano as administrator
- Log in to https://app.Kutano.com as an Owner or Administrator for your Kutano Workspace.
- In Kutano, navigate to Workspace admin -> Workspace settings using the sidebar.
- Scroll down to the Single sign-in section and click on the edit button
Sign in to Google Admin Console
- Open a new browser window.
- Log into Google Workspace Admin Console - https://admin.google.com
Setup Google SAML
- In Google Admin Console, navigate to the Menu → Apps → Web and mobile apps
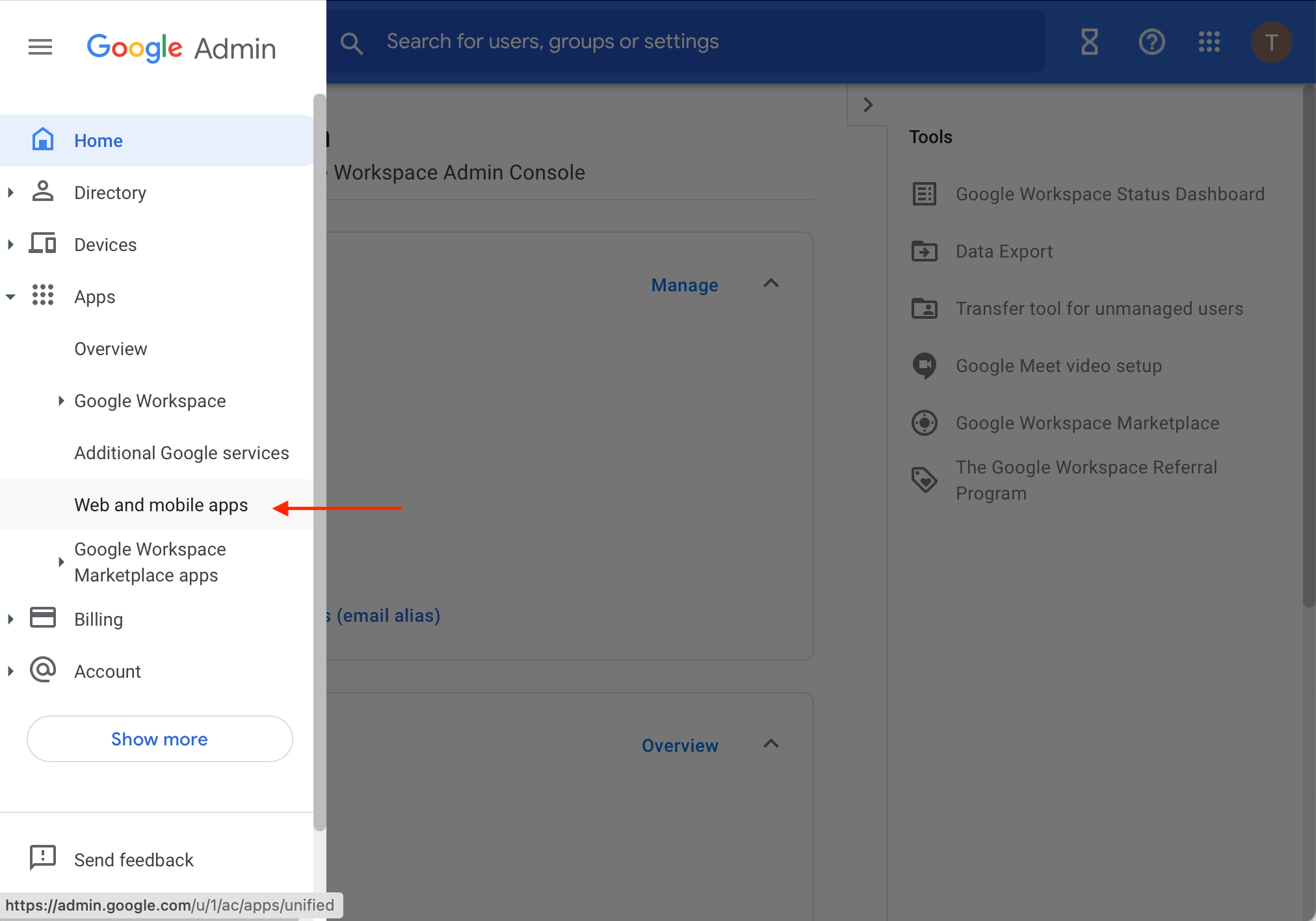
- Select the menu Add App → Add custom SAML app
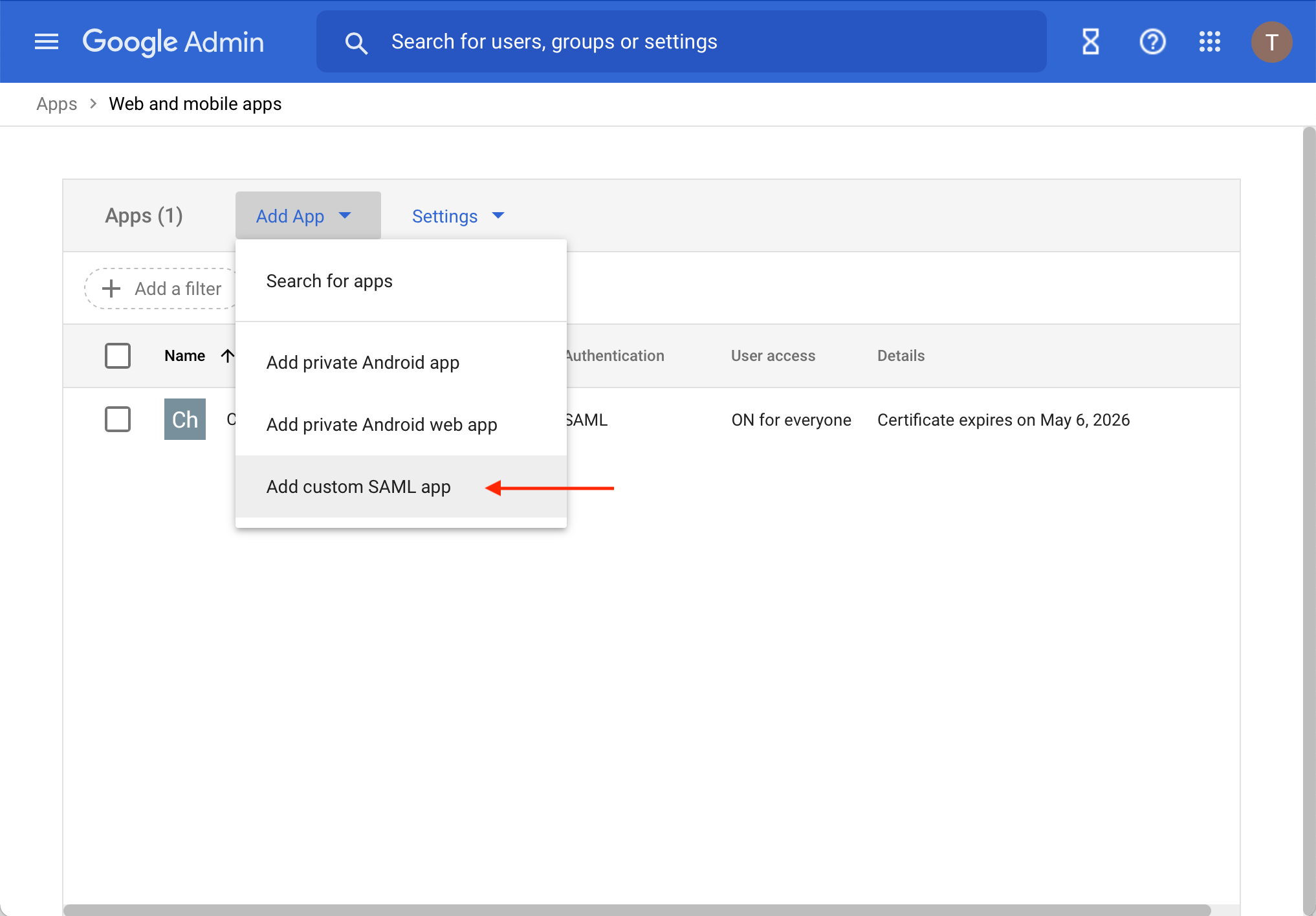
- On the App detail page, enter Kutano as the App name and select Continue.
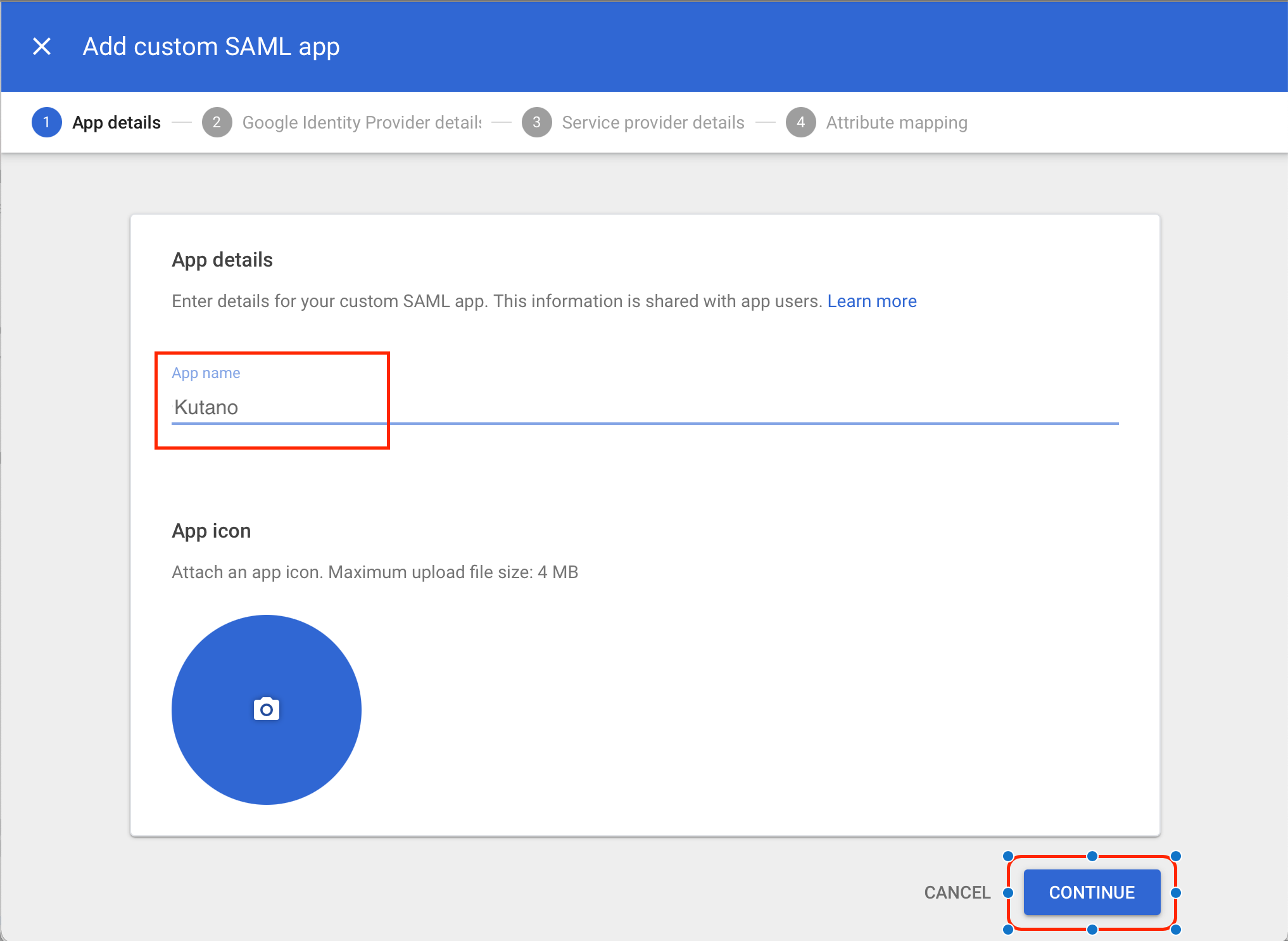
- In the next screen are the values you need for Kutano. Don't click the Continue button just yet.
- Copy the values from this page to the Kutano SAML setup page.Here are the where to put each value:
- SSO URL → SSO URL (Login Url)
- Entity ID → Entity ID
- Certificate → Certificate
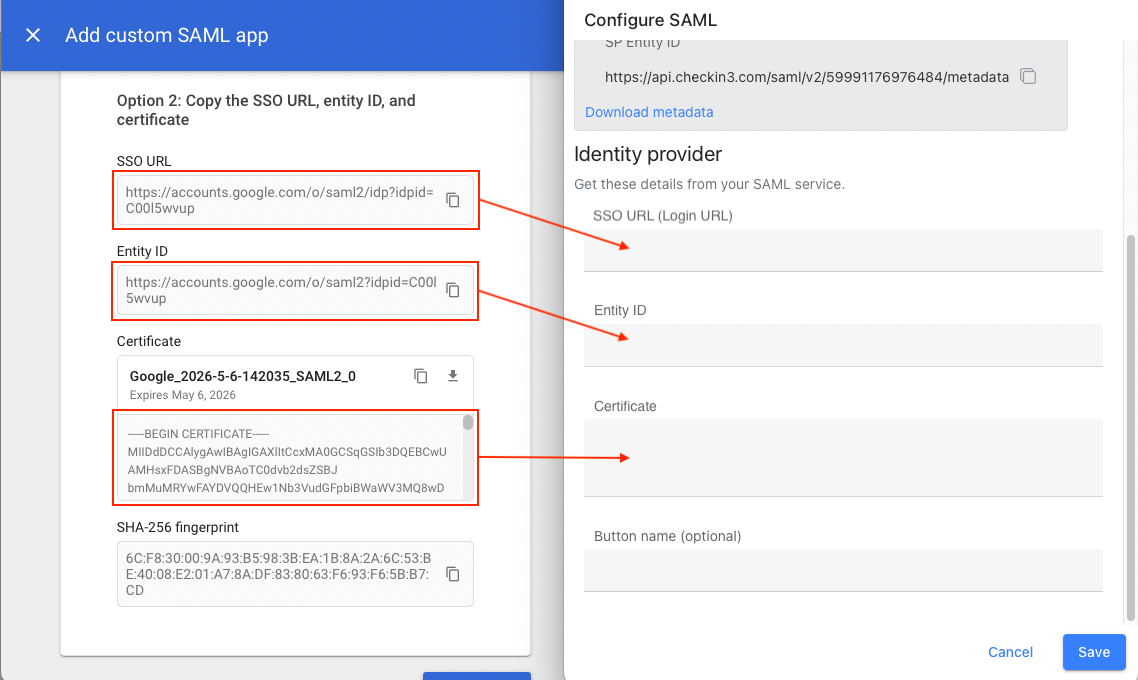
- In Google Admin, click the Continue button.
- Enter the ACS Url and Entity ID from that values found on the Kutano SAML setup screen.
- Set the Name Id format to EMAIL.
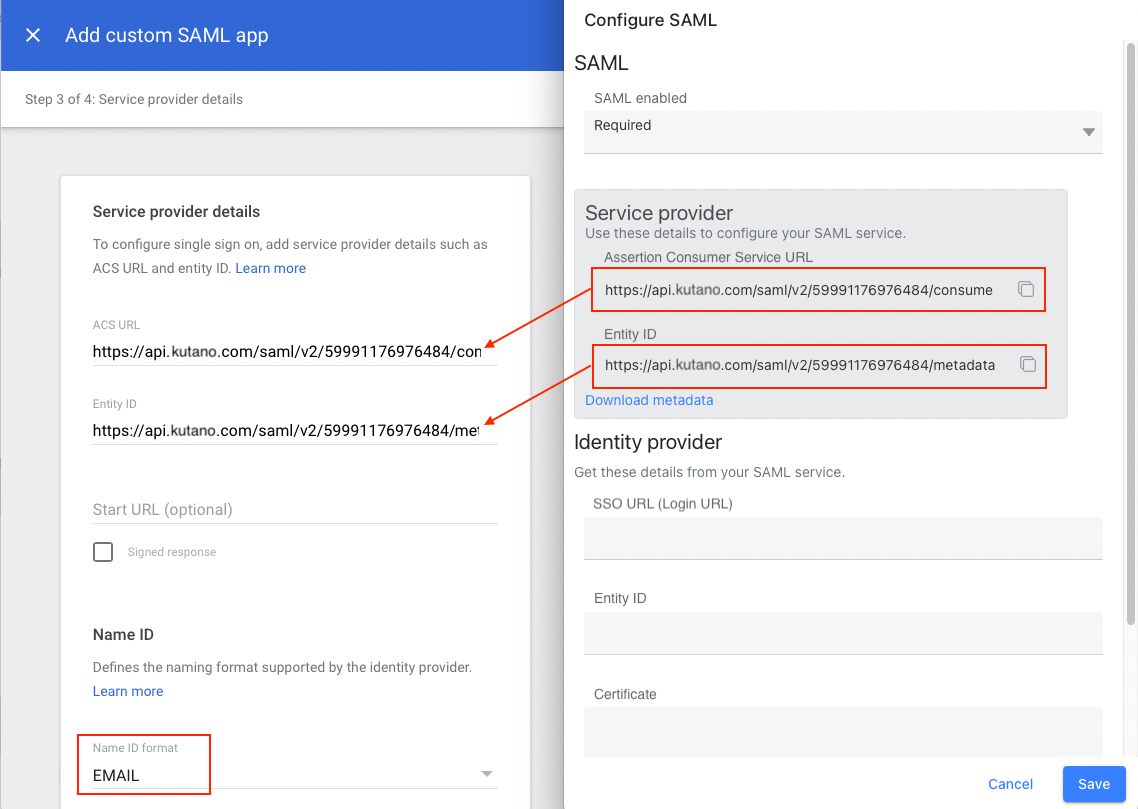
- In Google Admin, click the Continue button and then the Finish button
- In Kutano, click the Save button
SAML Attribute Mapping
To get the first and last name during the SAML process, the attribute mapping needs to be configured.
- In the Google Admin Console navigate to Kutano application page: Menu → Apps → Web and mobile apps → Kutano.
- In the SAML attribute mapping section, click on the SAML attribute mapping button.
 \
\ - In the SAML attribute mapping screen, click the ADD MAPPING button and enter the following information:
- Basic Information: First name
- App attribute: givenName
- Follow the above instructions for the following information:
- Basic Information: Last name
- App attribute: familyName
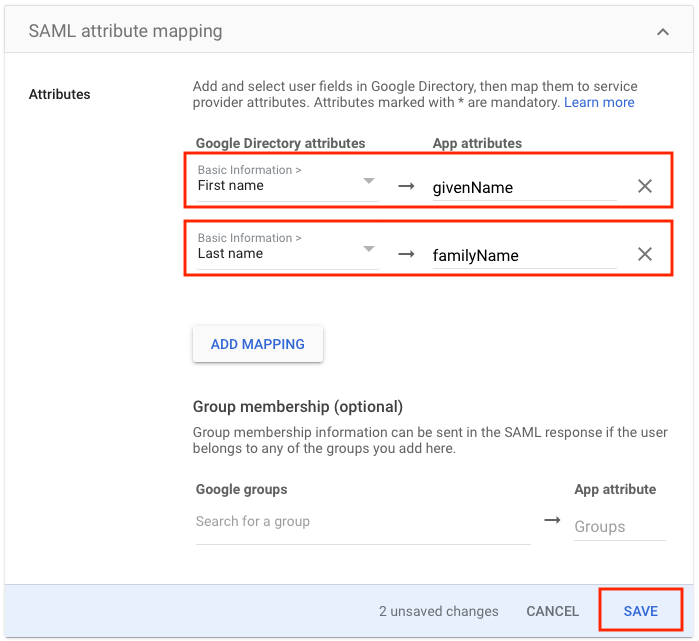
- Click the Save button
Enabling Access for Users in Google Workspace
Now that the Kutano SAML app is configured in Google Workspace Admin, access must be granted to Google users.
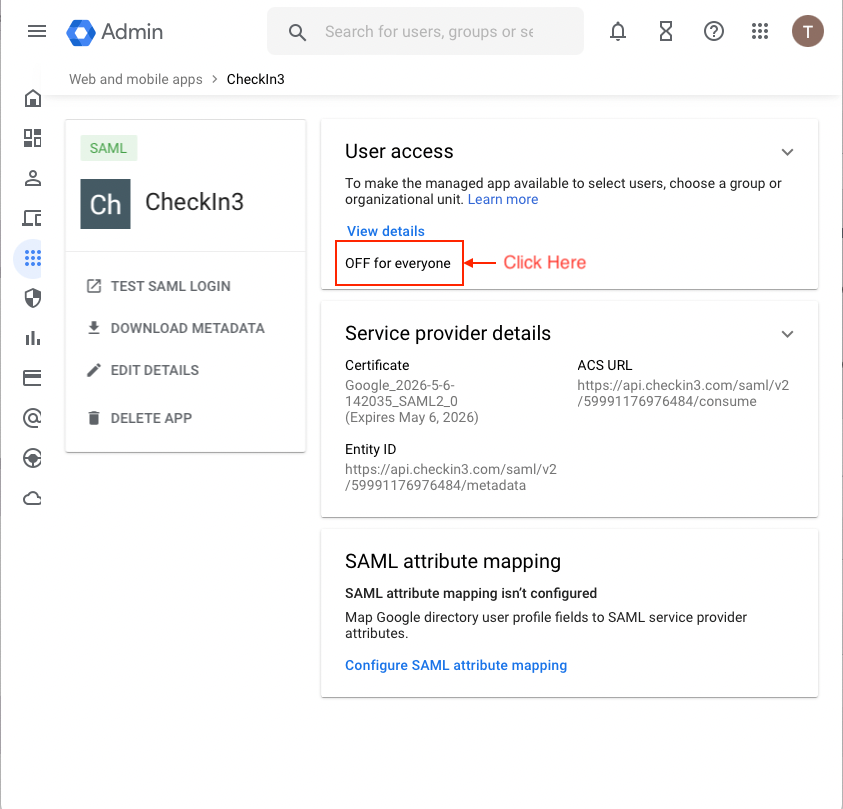
- In the Google Admin Console navigate to Kutano application page: Menu → Apps → Web and mobile apps → Kutano.
- In the User access section, click on the OFF for everyone label.
- In the Service Status screen, select All users in this account or the desired Groups or Organizational Units then select ON for everyone
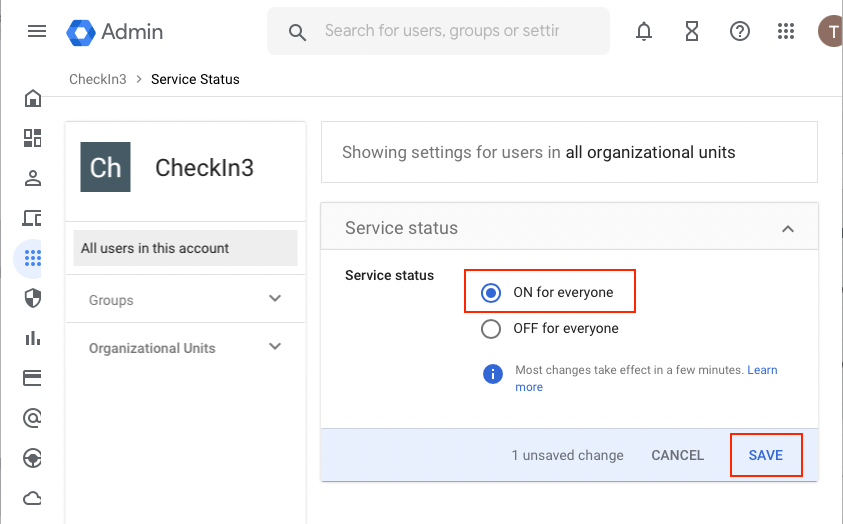
- Finally, click the Save button.
Testing Access
- Sign out of the Kutano application.
- In Google Admin Console, navigate to Kutano application (Menu → Apps → Web and mobile apps → Kutano)
- Click the TEST SAML LOGIN button
- Your browser should navigate to the Google sign in page. Select the correct account from the list.
- If everything works, you should be signed into Kutano and be redirected to your workspace's home page.
Finishing Up
-
When it is confirmed users can log in with SAML, you can restrict login to be via SAML only for all users in your domain by setting Require SSO on the SAML dialog in Kutano.
- Optional: Users can continue to log in with username/password or SSO
- Required: Users in your workspace who try to log in with username/password will be redirected to your IdP instead. For safety, the Kutano Workspace Owner and Admins will still be able to log in using their username/password even if this option is set to Required.
Extra information for Google Workspace users
- When it is confirmed that users can log in with SAML, you can restrict login to be via SAML only for all users by making the SAML Required instead of Optional in the SAML edit dialog in Kutano. For safety, the Workspace Owner and Admins will still be able to log in using their username/password after this option is set.
- Google Workspace does not send the session duration value in its SAML assertion. Kutano will expire and attempt session re-authentication at the duration chosen in the Kutano setting Session Timeout, on the SAML tab in Kutano's Workspace settings. The default value is to log out the user after one month.
- Google Workspace can sign either the Assertion or Response. Kutano will enforce a valid signature against the Google Workspace-generated IdP Public Certificate.
- Google Workspace does not support encrypting the Assertion. Kutano will accept unencrypted assertions.