SAML with Microsoft Entra ID
☝️ This feature is only available to workspaces using the Enterprise Plan.
If you haven't already, read up on the general setup of SAML with Kutano
Microsoft Entra ID (formerly Microsoft Azure Active Directory or Azure AD) is a Directory-as-a-Service provided by Microsoft Azure. Kutano's SAML SSO and user provisioning with SCIM are confirmed to work with Microsoft Entra ID.
Here's a walk-through of setting up Microsoft Entra ID as your SAML Identity Provider. This allows your team to log into Kutano without a new email / password combination, they just log in to your Azure user account.
Setup
It's a good idea to have Microsoft Entra ID and Kutano opened in separate browser windows or tabs so you can copy data from one web page to the other.
Sign in to Kutano as administrator
- Log in to https://app.Kutano.com as an Owner or Administrator for your Kutano Workspace.
- In Kutano, navigate to Workspace admin -> Workspace settings using the sidebar.
- Scroll down to the Single sign-in section and click on the edit button
Sign in to Microsoft Azure
- Open a new browser window.
- Log in as an administrator to https://portal.azure.com
Setup Microsoft Entra ID SAML
- Select Microsoft Entra ID in the main navigation panel
- Select Enterprise Applications from the subcategory panel
- Click the + New application button, and add a Non-gallery application.
- At the top of the Browse Microsoft Entra Gallery page click the + Create your own application button
- In the Create your own application dialog,
- What's the name of your app? Kutano
- Select Integrate any other application you don't find in the gallery (Non-gallery)
- Click Create button. You will be navigated to the newly created Enterprise Application page.
Assign Users to the App
- Click Users and groups on the left-side menu.
- Click '+ Add user/group'.
- Search for and select the users you’d like to assign Kutano access to. You can make multiple selections, and they will appear under Selected items.
- Click the Assign button
Enable Single Sign-on for the Enterprise Application
- Click Single Sign-On on the left-side menu.
- In the Single sign-on screen, click SAML to open the SSO configuration page.
- In Section 1 (Basic SAML Configuration), click Edit button
- Below Identifier (Entity ID), click the Add identifier button which will provide you with an input box.
- From Kutano SAML page copy the SP Entity ID value into the entry box.
- Below Reply URL (Assertion Consumer Service URL), click the Add identifier button which will provide you with an input box.
- From Kutano SAML page copy the SP ACS URL value into the entry box.
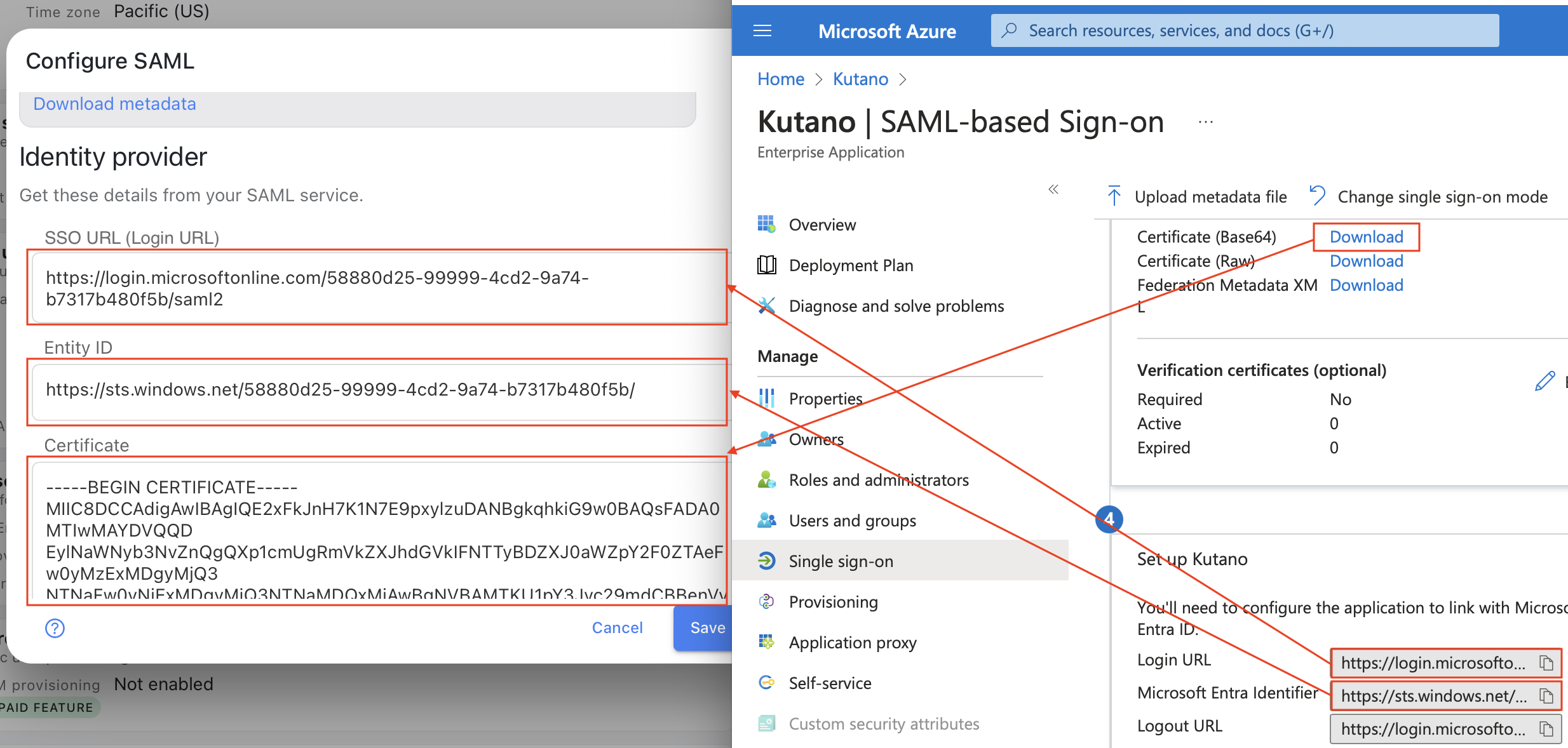
- Click Save button
- Close the Basic SAML Configuration dialog.
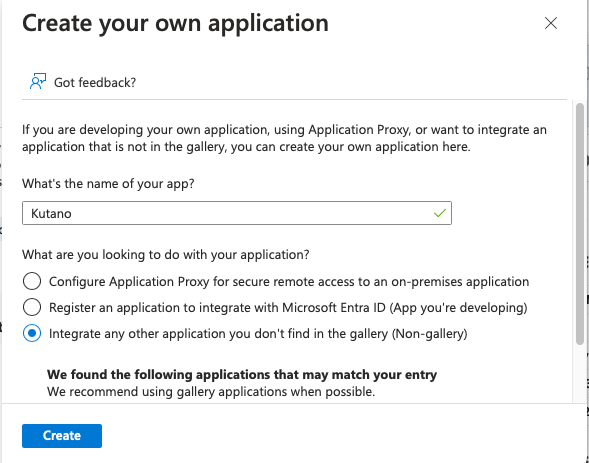
- In Section 3 (SAML Signing Certificate), click on the Download button next to Certificate (Base64). This will download a text file called Kutano.cer. Keep this file secure.
Configure Kutano
- In Microsoft Entra ID, locate Section 4 (Set up Kutano). Values in this section will be copied below.
- In the Kutano application's Configure SAML dialog, find the SAML enabled select button and choose 'Optional'.
- Scroll down to the Identity Provider section:
- Copy the string from the Microsoft Entra ID field Login URL into the Kutano field SSO URL (Login URL)
- Copy the string from the Microsoft Entra ID field Microsoft Entra Identifier into the Kutano field Entity ID
- Copy the contents of the Kutano.cer certificate file you downloaded into earlier into the Kutano field Certificate.
- Click the Save button in Kutano application's Configure SAML dialog.
Test the SAML Sign-in
NOTE: this test will attempt to sign you into Kutano using the currently signed in Microsoft user. Ensure that the Kutano workspace has this user's email setup as a valid user.
- In Microsoft Entra ID in Section 5 (Test single sign-on with Kutano), click on the Test button.
- In the next dialog, click on the Test sign-in button
- You should be redirected to your Kutano workspace and become signed in with current authenticated Microsoft user.
Finishing Up
-
When it is confirmed users can log in with SAML, you can restrict login to be via SAML only for all users in your domain by setting Require SSO on the SAML tab in Kutano.
- Optional: Users can continue to log in with username/password or SSO
- Require for All Members: Users in your workspace who try to log in with username/password will be redirected to your IdP instead. For safety, the Kutano Workspace Owner and Admins will still be able to log in using their username/password even if this option is set to Require.
Extra information for AAD Users
- AAD does not send the session duration value in its SAML assertion. Kutano will expire and attempt session re-authentication only at the duration chosen in the Kutano setting Session Timeout, on the SAML tab in Kutano’s Workspace settings. The default value is to never log out the user.
- AAD can optionally sign the Assertion. Kutano will verify the signature against the AAD-generated IdP Public Certificate.